Search K
Appearance
Appearance
.DpJ-1xPd.png)
WhiteIntel is a dark-web fueled search engine that offers free functionalities to check if a company or its customers have been compromised by stealer malwares.
Their primary goal of WhiteIntel is to combat account takeovers and ransomware attacks resulting from information-stealing malware.
You can check their website and try their engine for free at:
Welcome to HackTricks' comprehensive guide on Threat Modeling! Embark on an exploration of this critical aspect of cybersecurity, where we identify, understand, and strategize against potential vulnerabilities in a system. This thread serves as a step-by-step guide packed with real-world examples, helpful software, and easy-to-understand explanations. Ideal for both novices and experienced practitioners looking to fortify their cybersecurity defenses.
A Threat Model is typically represented as a diagram, image, or some other form of visual illustration that depicts the planned architecture or existing build of an application. It bears resemblance to a data flow diagram, but the key distinction lies in its security-oriented design.
Threat models often feature elements marked in red, symbolizing potential vulnerabilities, risks, or barriers. To streamline the process of risk identification, the CIA (Confidentiality, Integrity, Availability) triad is employed, forming the basis of many threat modeling methodologies, with STRIDE being one of the most common. However, the chosen methodology can vary depending on the specific context and requirements.
The CIA Triad is a widely recognized model in the field of information security, standing for Confidentiality, Integrity, and Availability. These three pillars form the foundation upon which many security measures and policies are built, including threat modeling methodologies.
There are several tools and software solutions available that can assist with the creation and management of threat models. Here are a few you might consider.
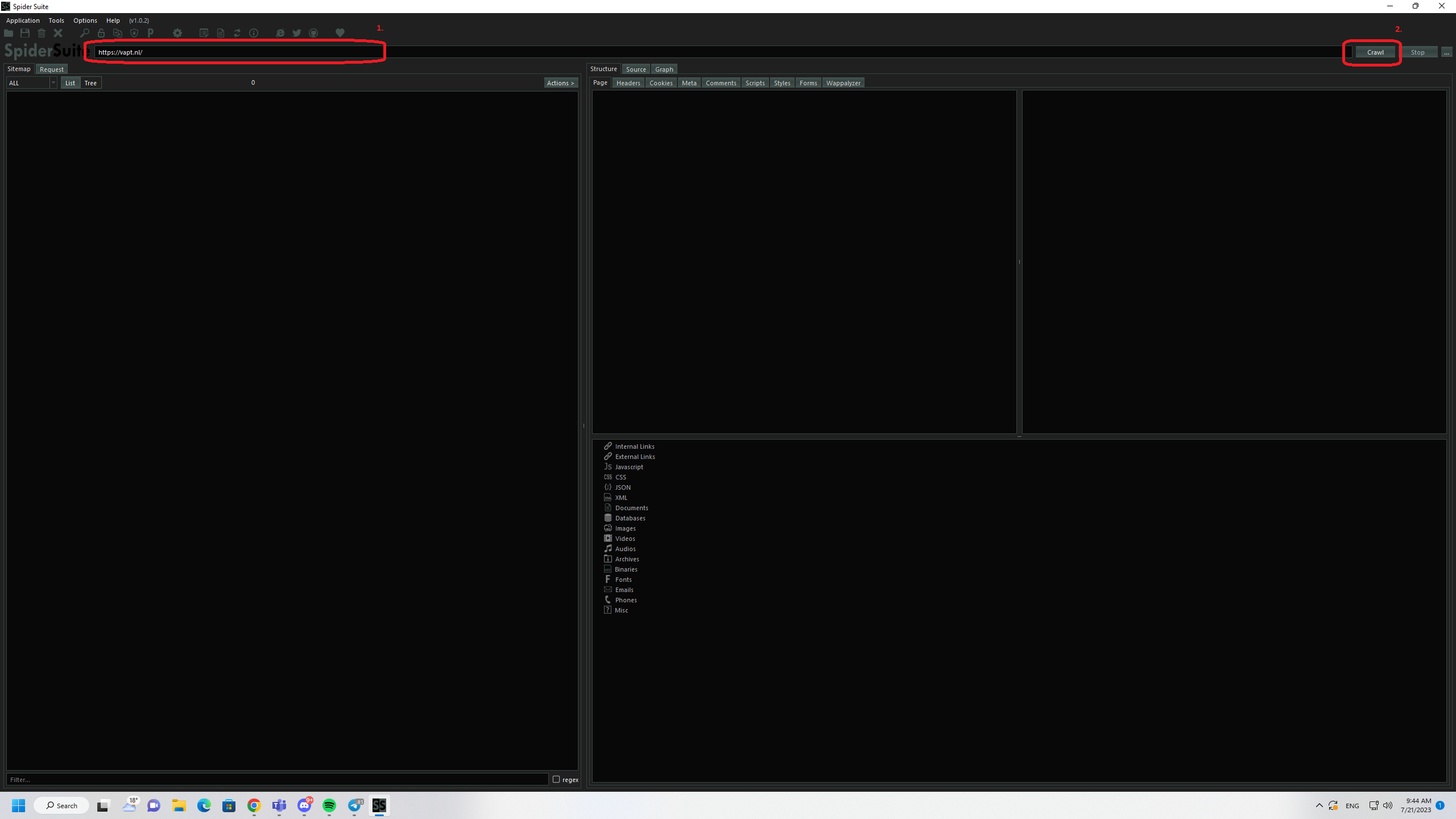
An advance cross-platform and multi-feature GUI web spider/crawler for cyber security professionals. Spider Suite can be used for attack surface mapping and analysis.
Usage
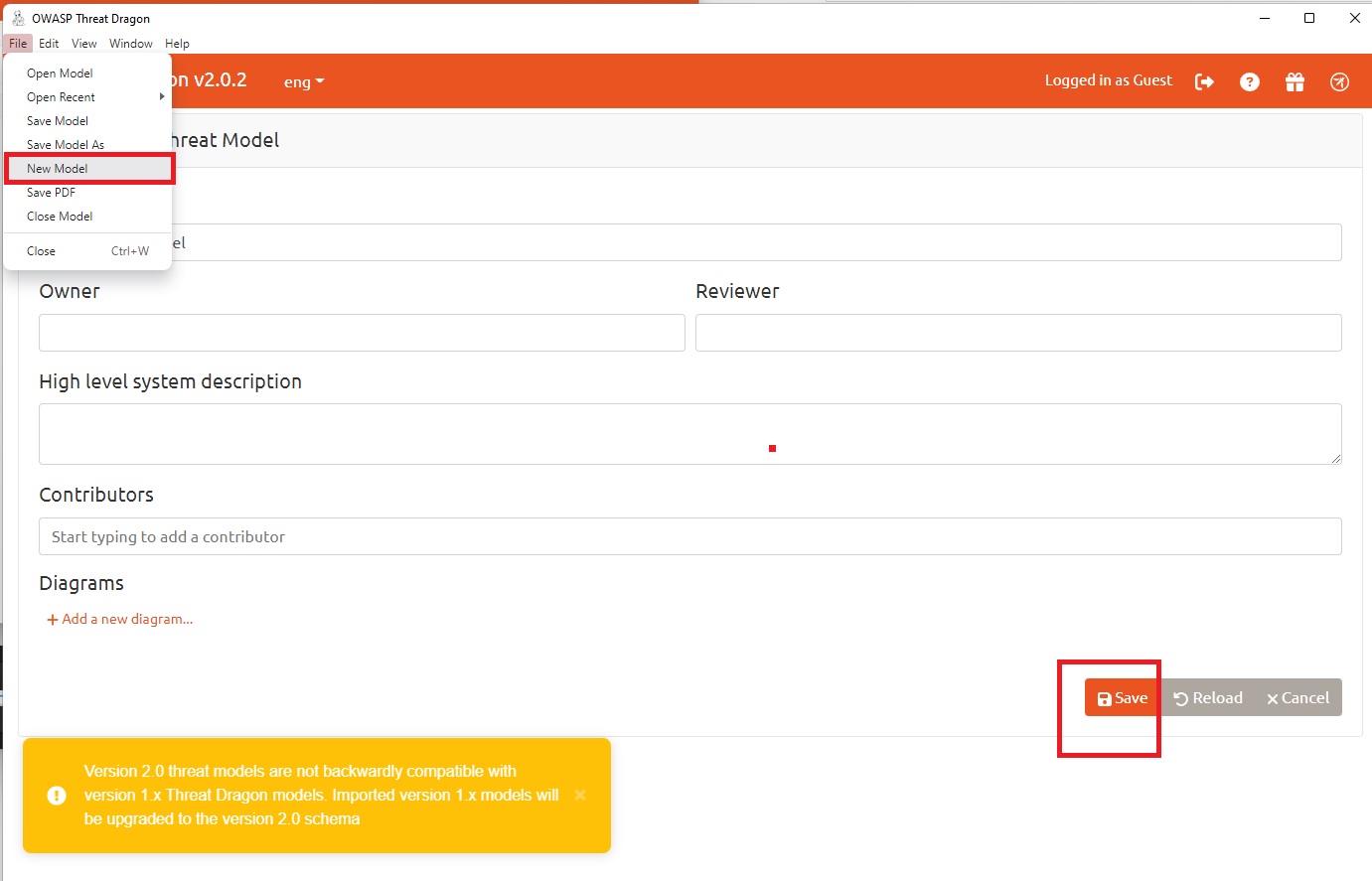
An open-source project from OWASP, Threat Dragon is both a web and desktop application that includes system diagramming as well as a rule engine to auto-generate threats/mitigations.
Usage
Sometimes it could look like this:
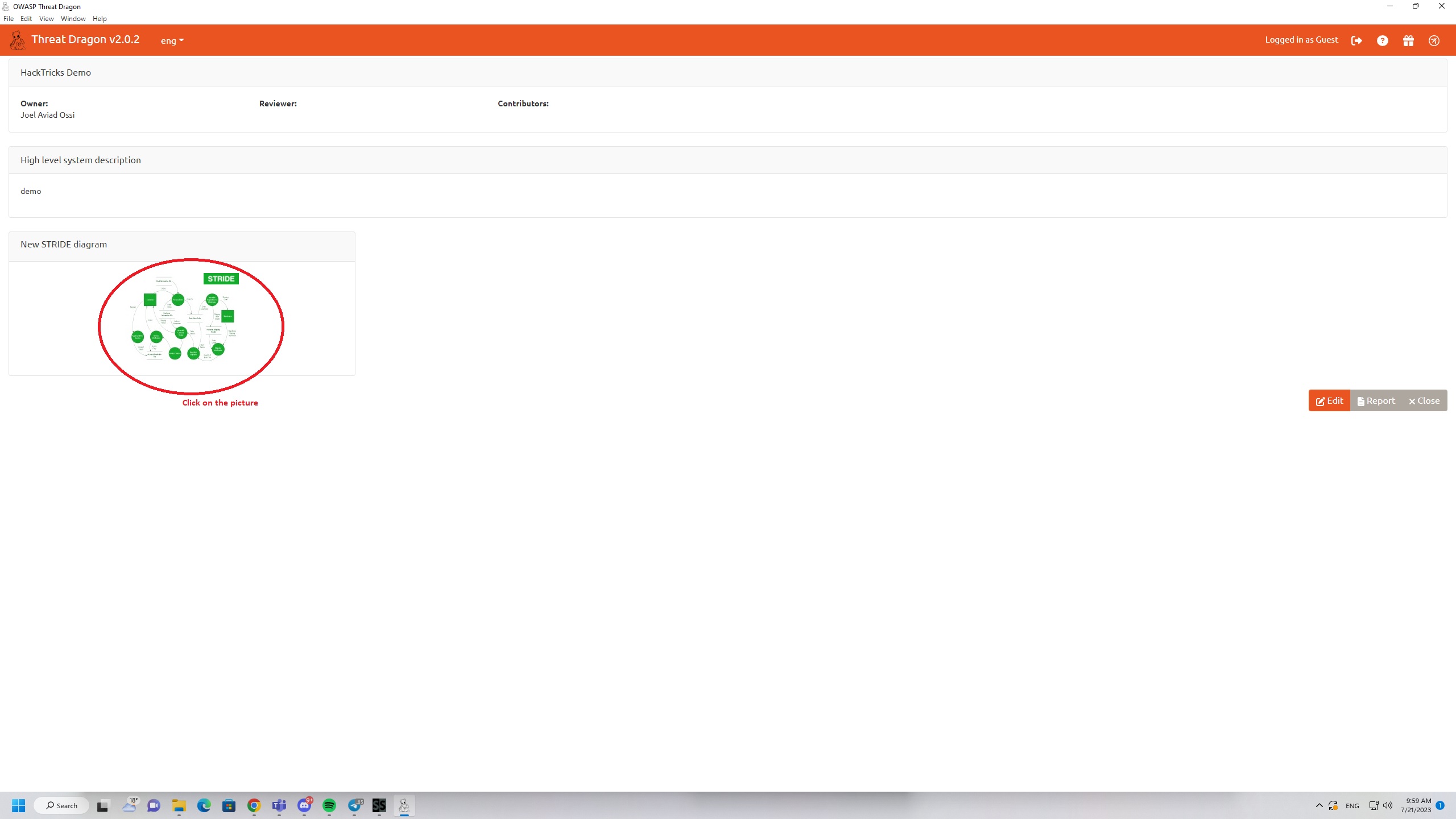
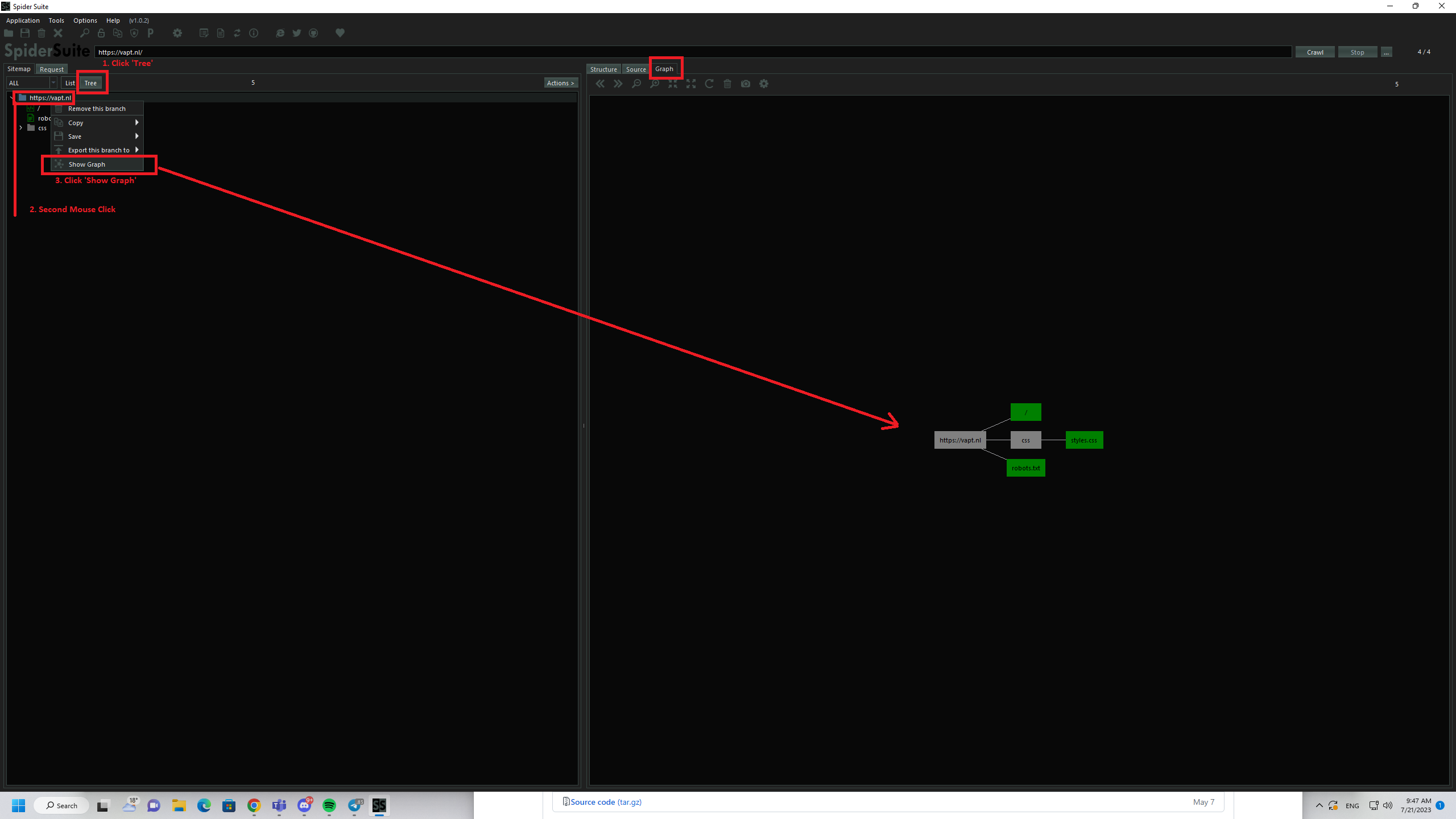
You can use tools like SpiderSuite Crawler to give you inspiration, a basic model would look something like this
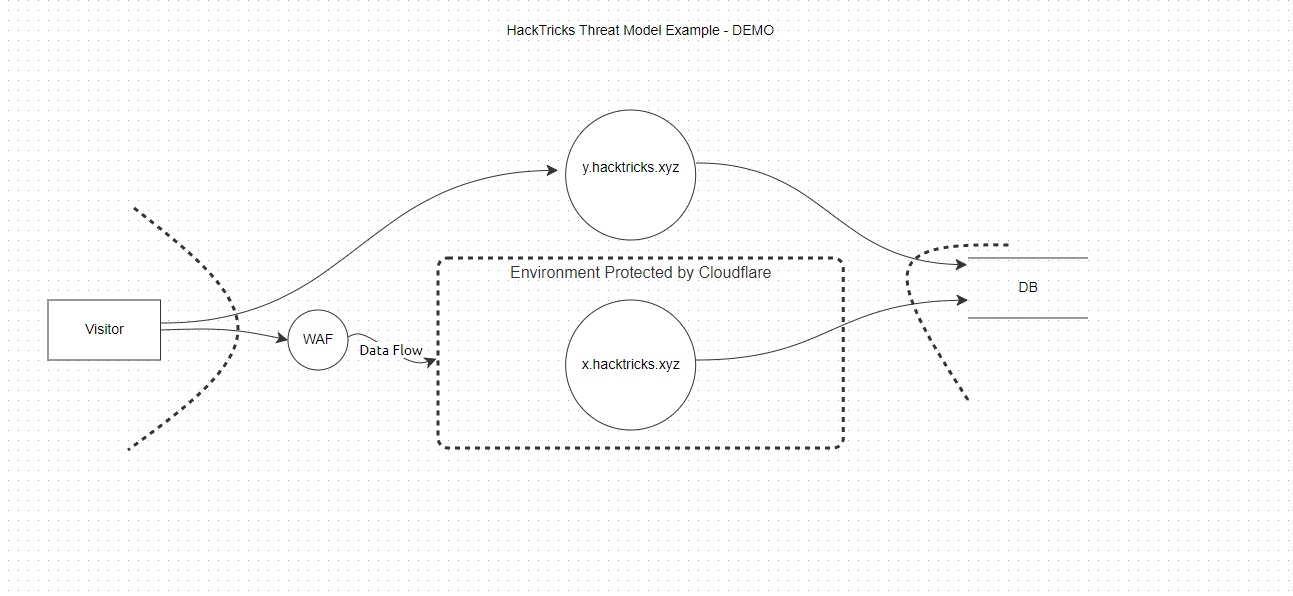
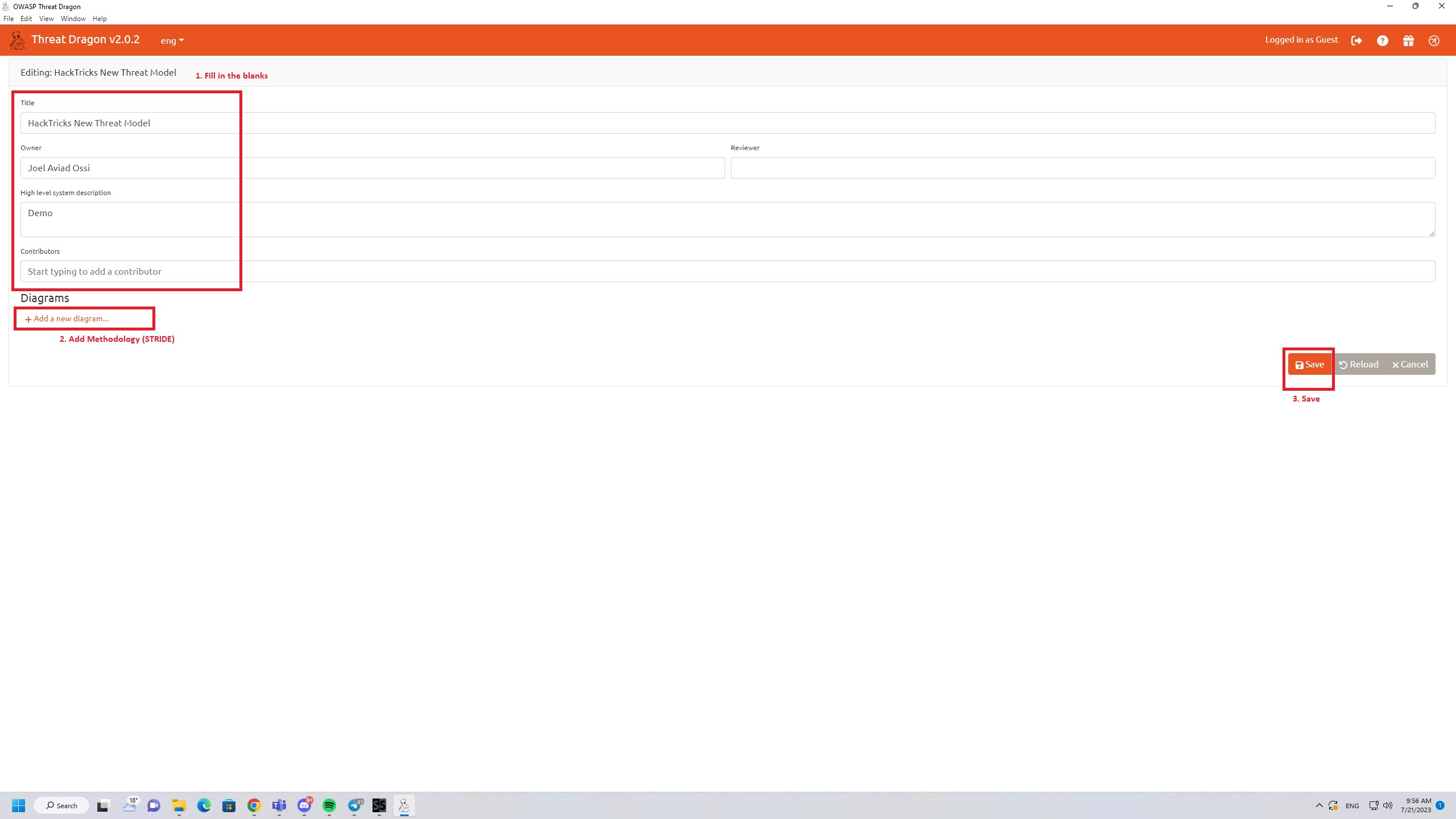
Just a little bit of explanation about the entities:
First you have to pick the layer you wish to add a threat to
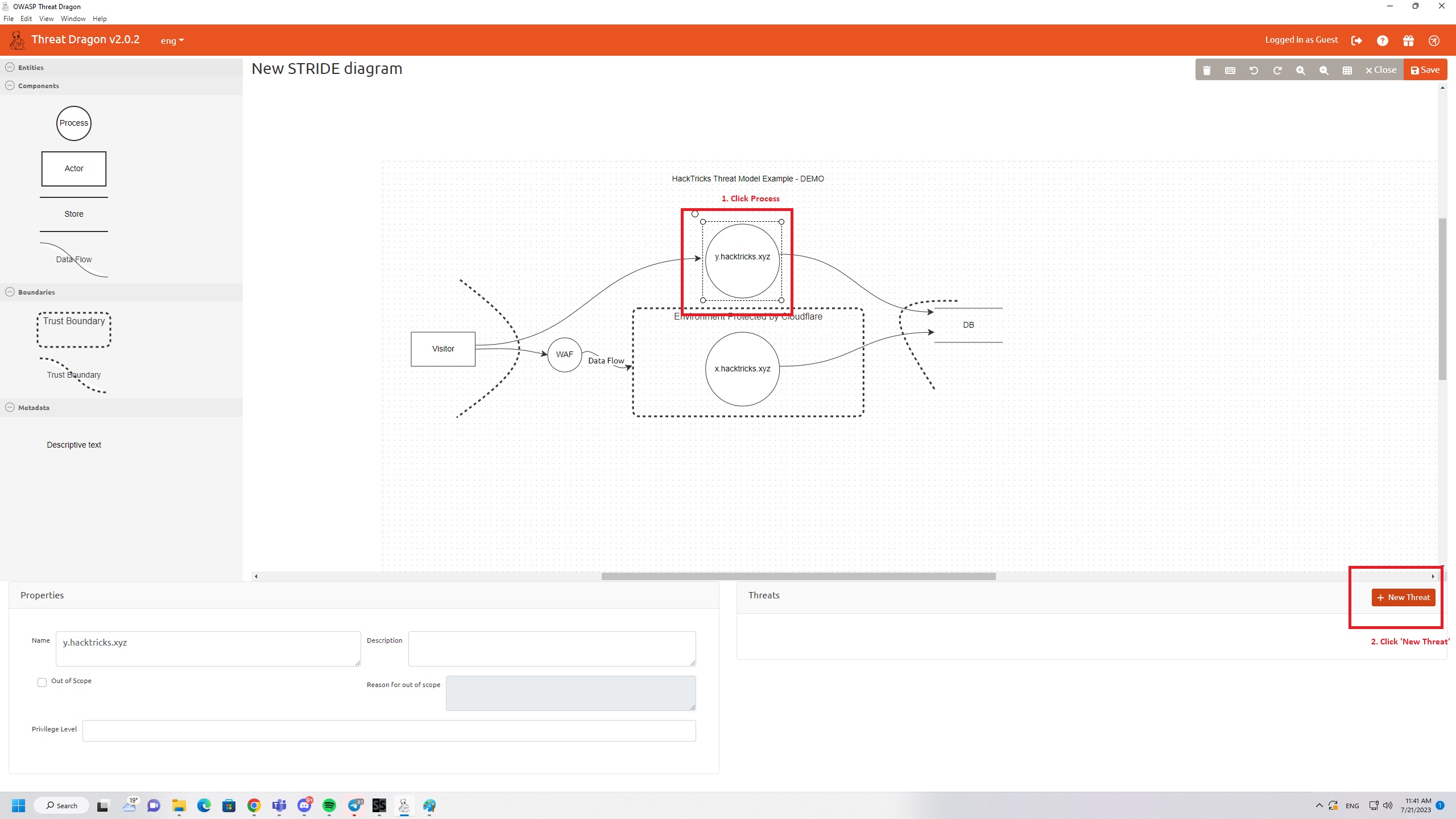
Now you can create the threat
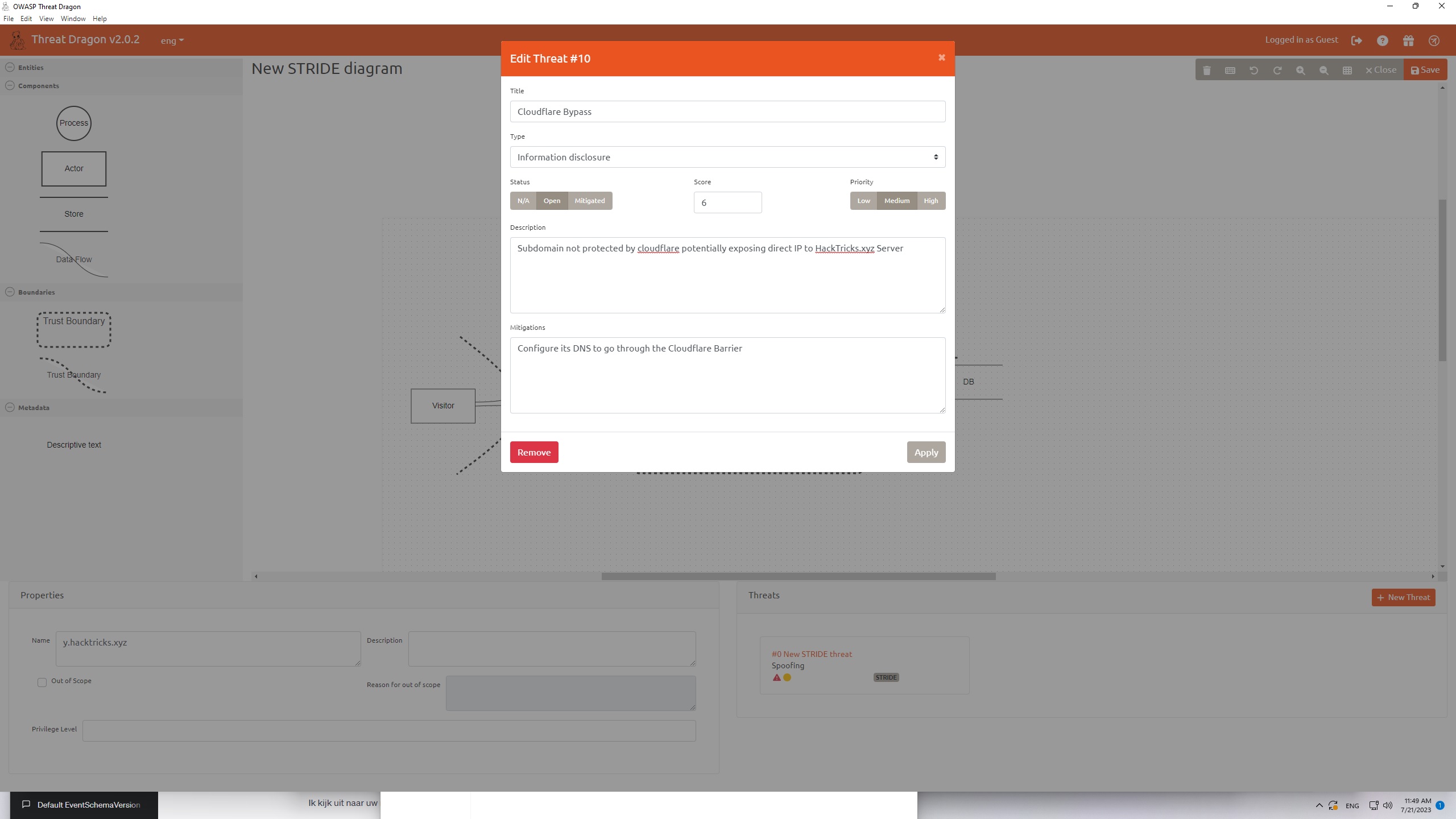
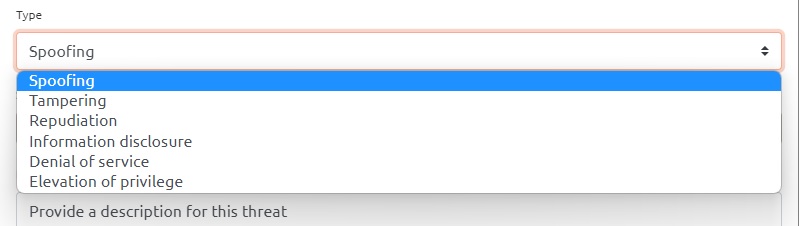
Keep in mind that there is a difference between Actor Threats and Process Threats. If you would add a threat to an Actor then you will only be able to choose "Spoofing" and "Repudiation. However in our example we add threat to a Process entity so we will see this in the threat creation box:
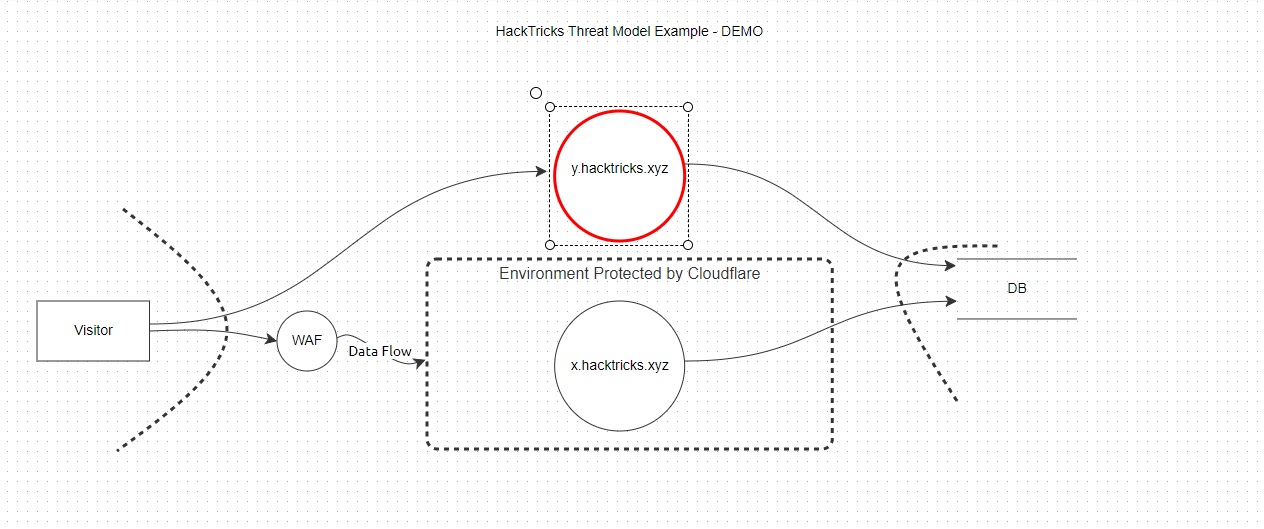
Now your finished model should look something like this. And this is how you make a simple threat model with OWASP Threat Dragon.
This is a free tool from Microsoft that helps in finding threats in the design phase of software projects. It uses the STRIDE methodology and is particularly suitable for those developing on Microsoft's stack.
.DpJ-1xPd.png)
WhiteIntel is a dark-web fueled search engine that offers free functionalities to check if a company or its customers have been compromised by stealer malwares.
Their primary goal of WhiteIntel is to combat account takeovers and ransomware attacks resulting from information-stealing malware.
You can check their website and try their engine for free at: