Search K
Appearance
Appearance
Other ways to support HackTricks:
.vYQDT_xE.png)
Join HackenProof Discord server to communicate with experienced hackers and bug bounty hunters!
Hacking Insights
Engage with content that delves into the thrill and challenges of hacking
Real-Time Hack News
Keep up-to-date with fast-paced hacking world through real-time news and insights
Latest Announcements
Stay informed with the newest bug bounties launching and crucial platform updates
Join us on Discord and start collaborating with top hackers today!
MongoDB is an open source database management system that uses a document-oriented database model to handle diverse forms of data. It offers flexibility and scalability for managing unstructured or semi-structured data in applications like big data analytics and content management. Default port: 27017, 27018
PORT STATE SERVICE VERSION
27017/tcp open mongodb MongoDB 2.6.9 2.6.9from pymongo import MongoClient
client = MongoClient(host, port, username=username, password=password)
client.server_info() #Basic info
#If you have admin access you can obtain more info
admin = client.admin
admin_info = admin.command("serverStatus")
cursor = client.list_databases()
for db in cursor:
print(db)
print(client[db["name"]].list_collection_names())
#If admin access, you could dump the database alsoSome MongoDB commnads:
show dbs
use <db>
show collections
db.<collection>.find() #Dump the collection
db.<collection>.count() #Number of records of the collection
db.current.find({"username":"admin"}) #Find in current db the username adminnmap -sV --script "mongo* and default" -p 27017 <IP> #By default all the nmap mongo enumerate scripts are used"mongodb server information""mongodb server information" -"partially enabled""mongodb server information" "partially enabled"By default mongo does not require password.
Admin is a common mongo database.
mongo <HOST>
mongo <HOST>:<PORT>
mongo <HOST>:<PORT>/<DB>
mongo <database> -u <username> -p '<password>'The nmap script: mongodb-brute will check if creds are needed.
nmap -n -sV --script mongodb-brute -p 27017 <ip>Look inside /opt/bitnami/mongodb/mongodb.conf to know if credentials are needed:
grep "noauth.*true" /opt/bitnami/mongodb/mongodb.conf | grep -v "^#" #Not needed
grep "auth.*true" /opt/bitnami/mongodb/mongodb.conf | grep -v "^#\|noauth" #Not neededExample from here.
Mongo Object IDs are 12-byte hexadecimal strings:
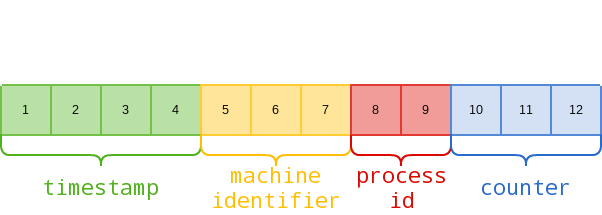
For example, here’s how we can dissect an actual Object ID returned by an application: 5f2459ac9fa6dc2500314019
Of the above elements, machine identifier will remain the same for as long as the database is running the same physical/virtual machine. Process ID will only change if the MongoDB process is restarted. Timestamp will be updated every second. The only challenge in guessing Object IDs by simply incrementing the counter and timestamp values, is the fact that Mongo DB generates Object IDs and assigns Object IDs at a system level.
The tool https://github.com/andresriancho/mongo-objectid-predict, given a starting Object ID (you can create an account and get a starting ID), it sends back about 1000 probable Object IDs that could have possibly been assigned to the next objects, so you just need to bruteforce them.
If you are root you can modify the mongodb.conf file so no credentials are needed (noauth = true) and login without credentials.
.vYQDT_xE.png)
Join HackenProof Discord server to communicate with experienced hackers and bug bounty hunters!
Hacking Insights
Engage with content that delves into the thrill and challenges of hacking
Real-Time Hack News
Keep up-to-date with fast-paced hacking world through real-time news and insights
Latest Announcements
Stay informed with the newest bug bounties launching and crucial platform updates
Join us on Discord and start collaborating with top hackers today!
Other ways to support HackTricks: