Search K
Appearance
Appearance
Other ways to support HackTricks:
For further information check the original post: https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing/. This is a summary:
If you don't know what Mach Messages are start checking this page:
For the moment remember that (definition from here):
Mach messages are sent over a mach port, which is a single receiver, multiple sender communication channel built into the mach kernel. Multiple processes can send messages to a mach port, but at any point only a single process can read from it. Just like file descriptors and sockets, mach ports are allocated and managed by the kernel and processes only see an integer, which they can use to indicate to the kernel which of their mach ports they want to use.
If you don't know how a XPC connection is established check:
What is interesting for you to know is that XPC’s abstraction is a one-to-one connection, but it is based on top of a technology which can have multiple senders, so:
Although the previous situation sounds promising there are some scenarios where this is not going to cause problems (from here):
-listener:shouldAcceptNewConnection: the audit token is safe). We are therefore looking for XPC connections that verify specific actions.Two different methods this might be exploitable:
xpc_connection_get_audit_token while not inside the event handler for a connection in a dispatch_async. Scenario:
A and B that we can both connect to (based on the sandbox profile and the authorization checks before accepting the connection).B can pass (but our app can’t). A obtains the audit token asynchronously, for example by calling xpc_connection_get_audit_token from dispatch_async.❌
In this case an attacker could trigger a Race Condition making a exploit that asks A to perform an action several times while making B send messages to A. When the RC is successful, the audit token of B will be copied in memory while the request of our exploit is being handled by A, giving it access to the privilege action only B could request.
This happened with A as smd and B as diagnosticd. The function SMJobBless from smb an be used to install a new privileged helper toot (as root). If a process running as root contact smd, no other checks will be performed.
Therefore, the service B is diagnosticd because it runs as root and can be used to monitor a process, so once monitoring has started, it will send multiple messages per second.
To perform the attack:
smd using the standard XPC protocol.diagnosticd. Contrary to normal procedure, rather than creating and sending two new mach ports, the client port send right is substituted with a duplicate of the send right associated with the smd connection.diagnosticd, but responses from diagnosticd are rerouted to smd. To smd, it appears as though the messages from both the user and diagnosticd are originating from the same connection.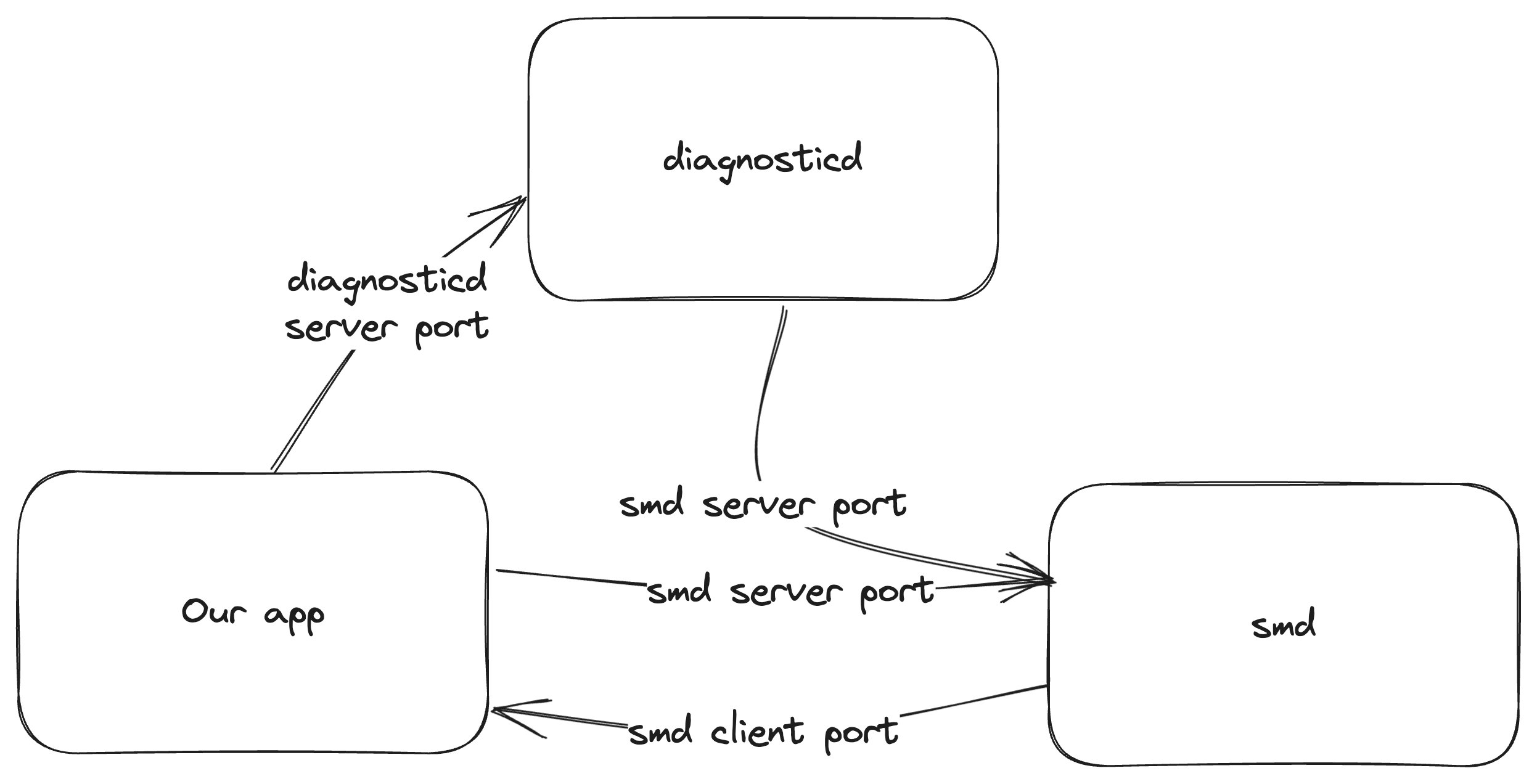
diagnosticd to initiate monitoring of a chosen process (potentially the user's own). Concurrently, a flood of routine 1004 messages is sent to smd. The intent here is to install a tool with elevated privileges.handle_bless function. The timing is critical: the xpc_connection_get_pid function call must return the PID of the user's process (as the privileged tool resides in the user's app bundle). However, the xpc_connection_get_audit_token function, specifically within the connection_is_authorized subroutine, must reference the audit token belonging to diagnosticd.In an XPC (Cross-Process Communication) environment, although event handlers don't execute concurrently, the handling of reply messages has a unique behavior. Specifically, two distinct methods exist for sending messages that expect a reply:
xpc_connection_send_message_with_reply: Here, the XPC message is received and processed on a designated queue.xpc_connection_send_message_with_reply_sync: Conversely, in this method, the XPC message is received and processed on the current dispatch queue.This distinction is crucial because it allows for the possibility of reply packets being parsed concurrently with the execution of an XPC event handler. Notably, while _xpc_connection_set_creds does implement locking to safeguard against the partial overwrite of the audit token, it does not extend this protection to the entire connection object. Consequently, this creates a vulnerability where the audit token can be replaced during the interval between the parsing of a packet and the execution of its event handler.
To exploit this vulnerability, the following setup is required:
A and B, both of which can establish a connection.A should include an authorization check for a specific action that only B can perform (the user's application cannot).A should send a message that anticipates a reply.B that it will respond to.The exploitation process involves the following steps:
A to send a message that expects a reply.A, the reply port is hijacked and used to send a message to service B.B.Below is a visual representation of the described attack scenario:
 (1) (1) (1) (1) (1) (1).png)
.CWkhpRCW.png)
xpc_connection_get_audit_token usage was challenging, both statically and dynamically.xpc_connection_get_audit_token function, filtering calls not originating from event handlers. However, this method was limited to the hooked process and required active usage.xpc_connection_get_audit_token from dispatch_async blocks were hindered by complexities in parsing blocks and interactions with the dyld shared cache.smd.smd by substituting xpc_connection_get_audit_token with xpc_dictionary_get_audit_token.xpc_dictionary_get_audit_token function is considered secure as it retrieves the audit token directly from the mach message tied to the received XPC message. However, it's not part of the public API, similar to xpc_connection_get_audit_token.setuid usage) might be a factor.Other ways to support HackTricks: